Trend Micro’s Zero Day Initiative (ZDI) is asking researchers to focus on server-side vulnerabilities through a new bug bounty addition.
On Tuesday, the research initiative said the Targeted Incentive Program (TIP), a new bolt-on to the already successful ZDI bug bounty program, will offer $1.5 million in “special bounty awards for specific targets.”
While ZDI has published over 600 security advisories based on bug bounty reports this year alone, according to Brian Gorenc, ZDI Director of Vulnerability Research, now is the time to start directing researchers “towards specific areas that either interest us or enhance protections for our customers.”
The team, in particular, want to start seeing more reports relating to critical class, server-side vulnerabilities — and they hope that the launch of TIP will cause an uptick in critical vulnerability reports which impact systems such as WordPress, Drupal, and Microsoft IIS.
However, the rules of the bug bounty addition are slightly different. The special financial reward is only available for a certain period of time — and will only be awarded to the first successful entry.
Starting 1 August, security researchers can enter reports for server-side systems. In the beginning, ZDI wishes to primarily focus on open-source products. For example, researchers have until the end of October to earn $35,000 to discover and report a critical vulnerability in WordPress, and until the end of January 2019 if they wish to hunt down exploits which impact Microsoft IIS.
The time frames and rewards for initial entries in the TIP program are below:
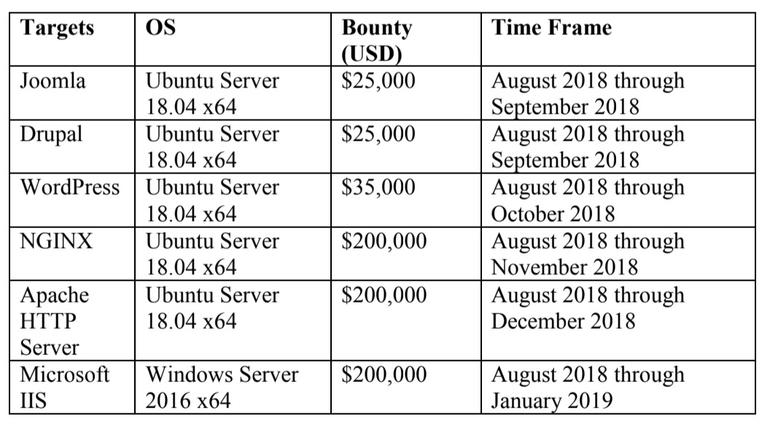
“The first researcher that provides a fully functioning exploit demonstrating remote code execution earns the full bounty amount,” Gorenc says. “Once the prize is claimed, the target will be removed from the list and a new target will be added to the target list.”
Entries must include fully functioning exploits and not just proof-of-concept (PoC) reports. In addition, valid bugs have to be zero-day vulnerabilities with the capacity to affect the core code of targets.
ZDI added that TPI entries must leverage either a vulnerability or a chain of bugs in order to modify the standard execution path of a program or process in order to allow the execution of arbitrary commands, bypassing the target’s mitigation defenses in the process.
These code executions can include, but are not limited to, Data Execution Prevention (DEP), Address Space Layout Randomization (ASLR) and application sandboxing.
Unless otherwise stated, bug bounty hunters must tailor their exploit search to the latest, fully-patched version of the target software.
As of now, ZDI has reserved over $1 million for bounties, including future targets which will be in the $200,000 — $250,000 range.
“The bugs targeted by this program represent some of the most widely used and relied upon software available,” Gorenc says. “We’re looking forward to finding — and eliminating — as many as possible.”
Reports submitted to TIP will be handed in the same way as Trend Micro’s current bug bounty program. Once notified, vendors will have 120 days to resolve security flaws.



