Threat Intelligence is one of the more important fields in the cyber security domain. Knowing your adversaries enables you as an organization to be one step ahead before actual cyber-attacks takes place. It is important to remember that there are two types of internet – the internet that we all know and the dark web which is used for malicious and illicit purposes.
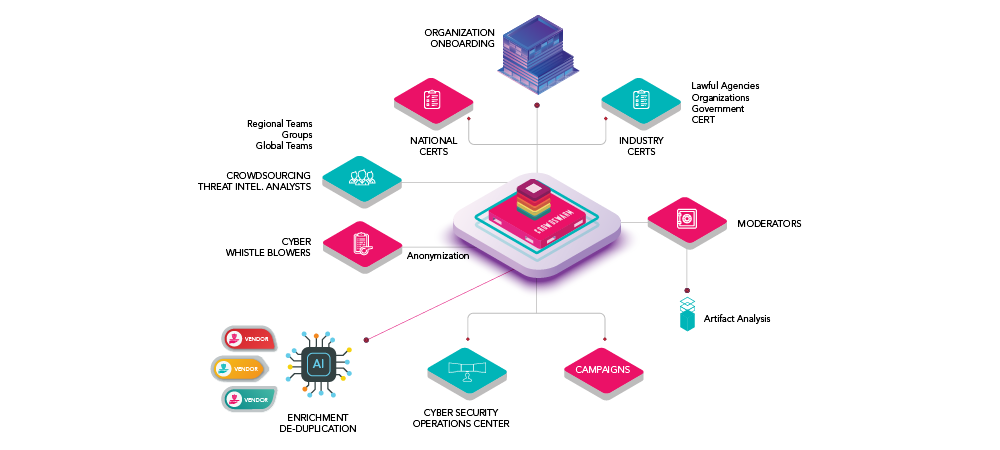
Crowdsourced Threat Intelligence / Vulnerability Disclosure Process Workflow
One of the common challenges vendors face is the ability to adopt a crowdsourcing model of cyber-threat analysts that cover the entire world. CROWDSWARM Threat Intelligence module provides multiple features and aims to solve many of the current challenges that exist within the current field of human-drive threat intelligence;
-
- Crowdsourcing threat intelligence analysts to provide human-driven threat intelligence services
- Work with existing threat intelligence vendors to provide enriched context of threats
- Threat intelligence vendors would publish their requirements on CROWDSWARM platform where they need support in performing deeper analysis on a specific hacking group
- Work with global Cyber Security Operation Centers who may require threat intelligence from our crowdsourced threat analysts pool on an on-demand basis
- CROWDSWARM Threat Intelligence Module would work with the following bodies;
- National and Regional CERT / SIRT teams
- Industry CERT / SIRT teams such as; ICS-CERT, FIRST
- Law Enforcement Agencies, Governments, CERTs,
- Industry sector leaders can publish requirements for specific threat intelligence campaigns they may be concerned about impacting their industry for research purposes “the threat actors impacting the maritime industry as an example”.
- Individual Cyber-Whistle Blowers

