Bug Bounty module in CROWDSWARM platform will allow organizations and businesses that want to launch new products or services to be tested for vulnerabilities prior to releasing it into production on the internet.
Using our intuitive approach of crowdsourcing talented cyber security professionals and penetration testers that have a digital reputation based on various factors, will have an opportunity to compete against each other to identify actual vulnerabilities of the system under test, for which they would be rewarded for based on the allocated bounty.
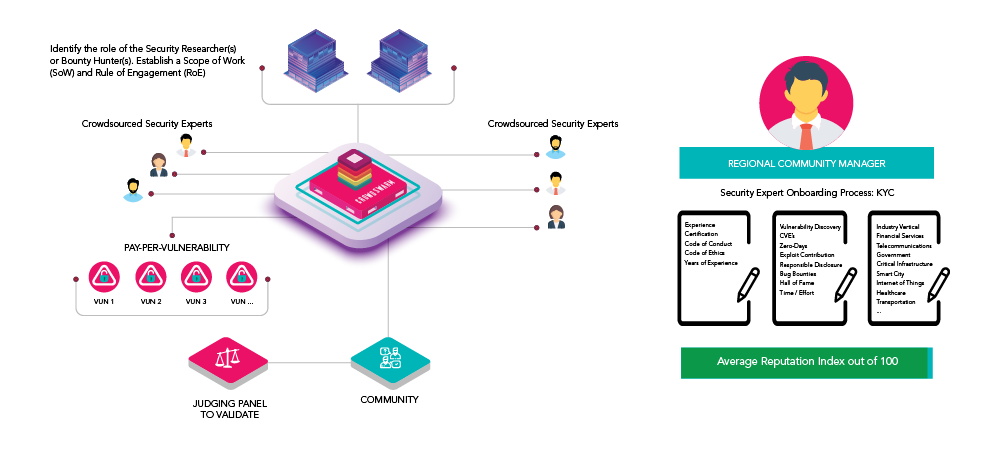
Crowdsourced Bug Bounty Process Workflow
Every organizational risk appetite varies and therefore organizations that may want a system to be tested that support critical business functions may be willing to pay more to find vulnerabilities compared to system that may not be so critical. This unique and novel approach of pay per criticality and pay per vulnerability through bug bounty program is what sets us apart.
Organizations that want new technology systems / products / applications to be tested, will subscribe to the bug bounty and place the bounty value. These bounty values will vary depending on the severity of the vulnerability, where critical exploit would be of the highest value.
Such conditions would form the basis of the smart contract, which would then attract the relevant security experts using our AI enabled crowdsourcing approach. Where the right pool of experts that match the conditions of the testing requirements would be notified.
Some of the key unique features of the bug bountry module include;
- Crowdsourcing security experts and creating a talent pool of various skill-set
- Every security expert will go through KYC and identity based validation and verification
- Security experts will have unique AI driven digital reputational algorithms to rank them
- Encourages new technology products, applications and services to be tested by crowdsourced security experts for flaws before blackhat hackers do
- Cost effective business model through pay-per-vulnerability as opposed to project basis
- Only approved security experts by the organization will be able to participate in the bug bounty
- Organizations will issue Rule of Engagement which security experts acknowledge
- CROWDSWARM Network will ensure only approved security experts will participate
- CROWDSWARM Network provides real-time progress update through leaderboard and risks identified
- Bug bounty is handled through escrow accounts using smart contracts
- Dispute management is performed by the judging panel – a collective community of masters in their respective domains

